Whispers from the Void: Scary Stories about Creepypasta Characters
Creepypasta came out as a genre of storytelling established around easily copied content which is then shared online and over and over collectively adapted or extended, sometimes namelessly, to create a shared mythology around a specific idea or creepypasta characters.
The theory of creepypasta has changed over time. In the very beginnings of the internet, the term was used to indicate a type of horror story namelessly on a place like 4Chan, which was then circulated on other forums and websites to scare, and entertain readers.

Popular Creepypasta Characters
Popular Creepypasta Characters
Below is a detailed overview of some of the most widely acknowledged and famous examples of Creepypasta characters, who or what they are expected to be, and where they came from. More complete details on the evolution and background of these particular creepypasta characters can be found at creepypasta.com.
Slenderman
Unquestionably one of the creepypasta characters that has entered most easily and universally into the mainstream imagination, Slenderman has been documented in numerous mass culture television shows and books and even had his big movie. It’s amazing because he was made on a message board without much planning.
Slenderman is often shown as a tall person in a suit, but his face is featureless and completely white, like a styrofoam mannequin head. Sometimes he’s represented with tentacles coming out from behind his suit or sleeves.
Jeff the Killer
Jeff the Killer is almost as popular as Slenderman, though not as widely featured in mainstream media. His fame grew mainly from being used in screamer videos, where he ends with his catchphrase “Go to Sleep” before attacking.
In looks, Jeff is a pale person without a nose, with an unnaturally wide, crazy grin and staring eyes without eyelids. He’s known for creeping into people’s bedrooms at night, saying his catchphrase, and then fatally stabbing them.
Ben Drowned
Ben Drowned is a highly popular Creepypasta character known for its impact on the entire genre. The character’s appearance is based on a creepy statue of Link from the Legend of Zelda games, featuring either empty eye sockets or bleeding eyes. This motif of taking existing characters and making them creepy by removing or altering their eyes is widespread. Examples include Sonic.exe, where Sonic has bleeding eyes and various versions of Simpsons or Spongebob characters similarly transformed into eerie figures.
The Rake
The Rake is a creepy creature from cryptid lore in Creepypasta. It’s said to haunt forests and has been accidentally caught on camera several times, notably on a motion capture camera meant for nocturnal animals. The most famous image of The Rake shows a pale, hairless creature moving in a hunched position. It looks humanoid with large, glowing eyes and a wide, gaping mouth.
The story of The Rake began with a suggestion on a message board to create a new monster. It first appeared on the personal blog of writer Brian Somerville in 2006. While the creature’s description seems linked to an image known as the ‘Berwick monster’ — which was mistakenly thought to be a real cryptid sighting but was actually a game still used for publicity — the timeline shows the story came before the image was associated with it.
Conclusion
Creepypasta is a genre that’s constantly changing and growing. It includes many characters, each with their own stories. What’s unique about creepypasta is that anyone can add to it or change it. This happens digitally, which means we can see how these characters evolve.
In the past, when stories were told orally, it took a lot of work to keep track of changes. With digital records, we can study these changes as they happen. This gives us new insights into why some parts of these stories stick around while others fade away.
Creepypasta is a new genre, but it has a lot of potential. It helps us understand how myths are created today and gives us clues about how myths were made and changed in the past.
Read More:
Movie123: Why Is It Free? Should You Watch Movies On It Or Not?
Why you shouldn’t be looking for Demon Slayer Season 5 Release Date? Because…
Recap: Season 4 Demon Slayer, cast, episodes, and more
Tekken 8 Mods: Everything You Need To Know
Hello Tekken lovers! Tekken 8 has been released very recently, but Tekken 8 mods are already appearing quickly. If you play on PC and want to try changing the look of your characters, stages, or interface, we’ve collected the best mods available. We’ve also provided the instructions on how to install them and also answered some frequently asked questions.

Tekken 8 Mods
Tekken 8 Mods
There are so many mods in Tekken 8, let’s have look on them:
- Tekken 8 HUD/UI mods – Players can change the interfaces of the game (e.g. create the stage selection screen look like a previous version)
- Tekken 8 costume mods – Players can add the latest costumes or clothing items to fighters (e.g. Calvin Klein Jun)
- Tekken 8 character mods – You can change the physical appearance of a character (e.g. make Kazuya look like CJ from GTA San Andreas)
- Tekken 8 stage mods – You can make totally new stages to fight on.
- Tekken 8 music mods – Players can change the background music.
How to install Tekken 8 Mods?
Forewarning, Tekken 8 mods only work on the PC version of Tekken 8. So, if you are playing on a gaming console, you won’t be able to use the mods. However, if you’re on PC be prepared as we have collected this step-by-step procedure for installing Tekken 8 mods:
- Discover a mod you prefer Nexusmods or Tekkenmods
- Download the mod and extract the files
- Drop the PAK file in Tekken8\Polaris\Content\Paks\Mods (you may need to make Mods folder)
- Start the game and enjoy
Be mindful that while installing a costume mod for a character, it will replace one of the existing outfits that the character owns. To learn about which outfit slot the mod will use, you should thoroughly read the mod description. This helps players to make a decision whether it’s worth replacing the existing outfit with the new one or not.

Some Popular Mods To Install
Some Popular Mods To Install
1. Tekken 8 Calvin Klein mods
A popular mod from Tekken 7 is back, enabling you to add new Calvin Klein underwear costumes for selected characters. The Tekken 8 version made by fine mod provides Calvin Klein, Reina and Jun.
2. Reina Devil Form
This is an amazing mod that gives Reina a complete Devil Form costume. The Reina Devil Form mod was made by VictorSelkovtsk. Reina’s Rage Art looks even more ill-natured in this outfit.
3. Kazuya as CJ from San Andreas
A Tekken 8 character mod that changes Kazuya into CJ from 2004’s Grand Theft Auto: San Andreas. To use this mod you need to make a custom preset with the motorcycle helmet, otherwise, you might see Kazuya’s head on CJ’s body. CJ San Andreas mod is made by Ercuallo.
4. Remove SSS (Super Smooth Skin) Mod
It is the most famous mod! “Remove SSS” has around 10,000 downloads. SSS means Super Smooth Skin, and activating this mode will significantly make your female characters more muscular and defined. You have the option of removing 50% or 80%. The Remove SSS Mod was made by Fine.
5. Move List Face Buttons Color Coding
A well-ordered mod that changes the color of buttons on your move list menu. This makes it easier and faster to see which buttons to press. You can opt between the Playstation and XBOX controller color schemes. The color scheme mod was created by peek6.

Improved Tekken 8 Visuals
Improved Tekken 8 Visuals
This capable mod by FrancisLouis enhances the clarity of the visuals in Tekken 8. When you use this mode you will observe how sharper and clearer the selection menu becomes as compared to the original blurry version.
To obtain this effect the Tekken 8 mod simply deactivates effects like bloom, film grain, and lens flare. It then activates two filters to sharpen and optimize the quality of the textures.
The Improved Visuals Mod also enables you to strengthen the internal resolution of the game up to a maximum of 200 (100 is the default).
Can my combatant see my Tekken 8 mods?
No, your combatant will not be able to see any Tekken 8 mods you have installed. This is a very common question, specifically as particular mods allow you to fight with nude fighters. There is nothing to worry about! Your combatant also happens to have the similar mod installed.
Can you get banned for using Tekken 8 mods?
No, you will not be disallowed for making use of mods that change the visuals of Tekken 8 like character appearance or UI. These visual mod changes are only seeable to you or fellow mod-users. Bandai Namco has typically ignored modding in their games.
Disclaimer
Modding Tekken 8 is solely for personal enjoyment. Mods alter game visuals and are only visible to users. Use at your own discretion; multiplayer fairness isn’t guaranteed.
Read More:
Playgd Mobi in 2024: What is this Gaming Platform and User Insights
How to redeem Fortnite Skins codes on PC, Xbox One, PS4, & Switch in ‘24!
Discover the Best Free Online Games for Endless Entertainment
How Many Megabytes In a Gigabyte? Easy Conversion Explained
Megabytes and gigabytes are both considered as storage measurement units. A gigabyte shows more capacity than a megabyte. How many megabytes in a gigabyte, then? This is defined by the system used to measure storage and there are two methods for converting MB to GB.
This explains why there can be a difference between the storage capacity advertised for a drive and the amount shown on your computer.

What is Megabyte?
What is Megabyte?
The megabyte is a unit to measure data storage. In other words, we can say that a unit we prefer to evaluate digital data with a value equal to a million bytes is known as a megabyte.
The byte is the main measuring unit for online data, but further definitions were needed to define the larger volumes of data; so, the megabyte was introduced.
What is Gigabyte?
A gigabyte is a particular unit of data that’s equal to around 1 billion bytes of data. The term gigabyte is generally used to determine the amount of stored data or the capacity of a storage device.
In respect of smaller units, a gigabyte is equal to 1,024 megabytes (MB). If you split a gigabyte into smaller units, you will have approximately 1,024 megabytes. However, a gigabyte represents 0.001 terabytes (TB). If you want to represent gigabyte in larger units, it would be approximately 0.001 terabytes.
How Many Megabytes in a Gigabyte?
There are 1,024 MB in 1 GB when making use of the binary approach. There’s also a second method to measure storage. For now, here’s a guide on converting binary prefixes:
- 1TB = 1,024GB
- 1GB = 1,024MB
- 1MB = 1,024KB
- 1KB = 1,024 Bytes
You’ll discover that your computer storage is most possibly measured in hundreds of gigabytes. SSD (solid state drives) and hard disc drives would possibly be measured in terabytes.
Your phone storage is also measured in gigabytes to store all of your photos, apps, and messages. You’ll observe that iPhones, for example, start at 64 GB.
Before moving ahead, let’s clarify something in case you’re puzzled about the 4 GB listed in your device’s features. Storage and memory (RAM) are two things that can be measured in gigabytes.
Storage is the place for long-term data, like files downloaded to use in the future. On the contrary, memory is only there to store short-term data while the file is being used.

What Are the Two Methods for Measuring Storage?
What Are the Two Methods for Measuring Storage?
There are two methods for demonstrating the appropriate value of a measurement unit. You can evaluate this using the International System of Units (SI) or the binary method, which is commonly used in electronic devices.
They represent two different measurements, where the binary method and the SI method differ by approximately 4.86%.
Converting Using SI
Following the SI (International System of Units), the prefix “Mega” multiplies by 10 or represents a million units. In SI, this signifies it uses the decimal system, based on powers of 10.
In this case, 1 Kilobyte equals 1,000 bytes, which makes 1 gigabyte equal 1,000 megabytes.
Converting Using Binary System
This method is commonly used with binary devices like computers, phones, and tablets. The binary system operates on base 2. In this system, the prefix ‘mega’ equals 1,048,576 bits, so one gigabyte is equivalent to 1,024 megabytes.
Let’s have a look at the representation to obtain a good understanding of how the binary system works:
21 = 2
22 = 4
23 = 8
24 = 16
In binary, each additional digit increases the number’s value by a power of two. For instance, 2 raised to the power of 10 equals 1,024.
This is the reason your hard drive reads at a reduced capacity than what you purchased. Suppose you purchased a 250GB external hard drive and your computer shows only 232 GB of free space for use.
Now, why does this happen? Technologically, the drive has a capacity of 250,000,000,000 bytes. To demonstrate the precise amount of storage space available, work backward through the units of measurement.
Begin by converting bytes to kilobytes, then kilobytes to megabytes, and megabytes to gigabytes. Multiply the whole storage capacity by 1,024 three times to obtain 232 GB.
As the capacity of the disk increases, the difference increases between the advertised size and what the computer displays.
Final Words
How many megabytes in a gigabyte? Following the common terminology there are 1,024 MB in 1GB. We hope now you have a basic understanding of how storage is measured and that you can calculate the capacity of your device easily.
Read More:
Whats MB Mean In Text: Understand With Examples
FidelityFX Super Resolution: Powering Better Gaming Experiences
Transforming Pixels into Reality How Image-to-3D Model Technology Works
WazirX Hacked: What You Need To Know!
Mumbai-found crypto exchange WazirX has terminated withdrawals from the platform after suffering a considerable major hacking attack. India’s most popular exchange verified the same in a statement on X, previously known as Twitter. WazirX observed withdrawals in early European hours on Thursday (July 18). Wazir X, which widely designates itself as the ‘India Ka Bitcoin Exchange’, mainly targets the Indian market.
It is one of the few exchanges registered with the Financial Intelligence Unit (FIU) in the country, enabling it to provide crypto exchange services to citizens of India.
The company called the security violation a “force majeure event” that has allegedly resulted in the loss of $230 million. “This is a force majeure event that was beyond our control, but we are going to move heaven and earth and recover the funds. We have already blocked a few deposits and are in touch with concerned wallets for recovery. We are in connection with the best possible resources to help us in this attempt,” WazirX said in a statement posted on its X account.
The cyber attack took place because of a discrepancy between the data shown on Liminal’s interface and the transaction’s real contents, WazirX stated in a statement on Thursday. “At the time of the cyber attack, the information was dissimilar on Liminal’s interface and what was actually signed. We are doubtful the payload was replaced to transfer control of the wallet to a scammer.”
What makes $230 million in looted funds significant
What makes $230 million in looted funds significant
Following the reports, the platform has lost around $230 million. What makes the missing assets considerable for WazirX is that the company announced possessions of around $500 million in its June proof-of-reserves announcement. This signifies that WazirX has lost nearly half its reserves. Under Cyvers’ evaluation, the amount lost from the multiple-signature wallet on WazirX would be one of the significant loots in recent years.
What has been looted from WazirX
A third-party blockchain surveyor, Lookchain, reported that 200+ cryptocurrencies, including 5.43 billion SHIB tokens, around 15,200 Ethereum tokens, 20.5 million Matic tokens, 640 billion Pepe tokens, 5.79 million USDT, and 135 million Gala tokens were “looted” from the platform.

What about WazirX’s biggest competitors
What about WazirX’s biggest competitors
There are two other popular crypto exchanges in India – CoinSwitch & CoinDCX. The two companies guaranteed their consumers that their funds were secure and untouched by this incident. “Our wallet security remains unbreakable,” Sumit Gupta, co-founder and CEO of CoinDCX, posted on X (Twitter. )
“We suggest all our crypto investors be aware of possible market volatility during this time and practice caution in their trading and investment activities,” tweeted Ashish Singhal, co-founder and chief executive of PeepalCo, the group holding firm of CoinSwitch.
What does the investigation reportedly say?
Following the media reports quoting Blockchain sleuth Elliptic, the North Korea-linked scammers seem to be blamed for the attack. The breach of a private key providing a way into the wallet reportedly led to the lack. The leaked private keys reportedly are used to upgrade a safe multi-sig wallet, which possesses noteworthy assets, to a harmful contract.
Read More:
Lucky Block Crypto Casino Overview: Sign Up, Games, Bonus, & Crypto Twist!
4 Most Popular And Widely Used Cryptocurrencies For Online Casinos
Crypto Futures vs Options: Understanding the Difference
Wiz Cybersecurity Declines $23 Billion Acquisition Bid From Google – Report
Wiz, Cyber security startup has reportedly declined a multi-billion dollar acquisition offer from Alphabet’s Google. Instead, they’ve chosen to go public with their company.
Following CNBC, it received a memo to Wiz employees from co-founder Assaf Rappaport, in which he demonstrated the decision to move out of the “humbling” $23 billion approach from Google.
Google’s approach to Wiz has been mentioned by different media outlets for weeks now, and if it had gone forward, it would have been Google’s most substantial acquisition ever.

Wiz rejection
Wiz rejection
It should be acknowledged that Google’s largest acquisition until now was the $12.5 billion purchase of Motorola Mobility in 20212, mostly because Mototrola’s patents were essential for the Android platform.
Motorola Mobility, which used to handle Motorola’s phones, was split from its main business division in December 2010.
However, Google sold Motorola to Lenovo for $2.9 billion in January 2014.
Google’s second-highest acquisition was buying the $5.4 billion cybersecurity veteran Mandiant in 2022.
But at present following the CNBC report, Google’s $23 billion proposal has been declined by the cybersecurity firm.
According to a staff memo obtained by CNBC, Wiz co-founder Assaf Rappaport wrote that “refusing such a humble offer is heavy.” A person close to Wiz’s concept, who asked namelessness to discuss personal matters willingly, stated the company weighed antitrust and investor worries as reasons for declining the deal.
According to the report, Rappaport wrote that the organization would focus on its next endeavors: going public for the first time and generating $1 billion in revenue every year
Wiz had been aiming both targets competently before talks with Google had been reported.
The deal would have almost doubled the startup’s value to $12 billion from its latest funding round, as noted by CNBC.

IPO Objectives
IPO Objectives
New York-founded Wiz was established in 2020 and has expanded quickly under Rappaport leadership. As recently as May, he had been targeting for an IPO.
Following CNBC, the company reached $100 million in annual recurring revenue in 18 months and reached $350 million last year.
Wiz’s cloud security products comprise prevention, active detection, and response, and are working toward cloud-based operations.
The objective of buying Wiz was to strengthen Alphabet’s position in the cloud computing market, which is currently dominated by Amazon Web Services and Microsoft.
Following CNBC, Google didn’t immediately reply to requests for comment.
HubSpot deal
Wiz was not the only company on Alphabet’s target recently.
At the beginning of the month Alphabet reportedly chose not to pursue an acquisition of HubSpot, due to heightened regulatory scrutiny of tech acquisitions for antitrust reasons.
That acquisition came about in April 2024 when reports surfaced that Alphabet was considering buying HubSpot to strengthen its position in CRM and cloud services.

Wiz: Great Future Without Google Acquisition
Wiz: Great Future Without Google Acquisition
Jay McBain, chief analyst at Canalys, said Wiz rejecting Alphabet’s offer reminds him of when Facebook CEO Mark Zuckerberg declined the $1-billion proposal from Yahoo and later exceeded a trillion dollars in worth.
Wiz has strong roots in an industry going ahead by double digits (for the anticipated future) and could influence public market capital in a way that Google wouldn’t provide,’ he said.
Matthew Ball, chief analyst at Canalys, said much of Wiz’s accomplishment has been in the Amazon Web Services (AWS) ecosystem.
“After the $1 billion funding round earlier this year, Wiz is well-resourced to keep executing its M&A strategy, work towards the direction of IPO and grow its value,” he said.
When asked about how Google’s acquisition would affect their partners, Canalys analyst Peter Bryan said that untangling the close relationships with other cloud providers would have been too challenging from an integration standpoint.
(Canalys is owned by Informa, which is the parent company of Channel Futures.)
Read More:
Crowdstrike Outage: The company that caused the global Microsoft outage in 2024
Overview of CrowdStrike Falcon: A comprehensive detail in 2024
Disney Hack in 2024: A massive attack on the Entertainment Kingdom!
The Guide To MeWe Login: How To Access & Explore the Platform
MeWe has earned popularity on social media for its priority on privacy and user control. If you are new to MeWe or want to understand more about the platform, in this guide you will learn step by step the process of MeWe Login, key features, and everything you need to know. So, without any further ado let’s start understanding MeWe.

How to Create a MeWe Account
How to Create a MeWe Account
Creating an account on MeWe is an easy process of just a few simple steps. To start follow these steps:
- Go to the official MeWe website or download the app from your app store.
- Open the app and find the “Sign Up” button on the homepage.
- Click on “Sign Up.”
- Enter your email address or phone number.
- Choose a password.
- Click “Create Account.”
- Check your phone or email for a verification code.
- Enter the code when prompted.
Mewe Login
Once your profile is created, logging into MeWe is a very simple process:
- Go to the MeWe homepage or open the app.
- Find the login form on the screen.
- Enter your email address or phone number.
- Type in your password.
- Click on “Log in.”
If you forget your password later:
- Click on “Forgot Password?” on the login page.
- Follow the instructions to reset your password and regain access to your account.

What Makes the MeWe Social Network Different?
What Makes the MeWe Social Network Different?
- MeWe focus strongly on privacy. It promises not to collect user data for mining or sell it to other companies.
- MeWe hasn’t shown personalized ads anymore since 2020. It funds itself through Pro subscriptions and sales of digital items like stickers and badges.
- Additional funds can be generated through options like cloud storage and video calling packages.
- MeWe Pro is a premium option for $5 a month (first month free) offering 100GB cloud storage, unlimited voice/video calls, extra emojis and stickers, custom profile themes, and badges.
- There are no post-boosting features or algorithmic management of content visibility.
- When you follow a page, or artist, or join a group, you see all their posts in the order they are posted.
- You have control over what appears on your timeline without content blocking or filtering based on algorithms or MeWe staff.
Understanding the Features of Mewe
The features which MeWe offers are as follows:
- The primary feature is its attention to privacy, MeWe does not monitor or sell user data to advertisers which signifies your personal information remains private and safe.
- Another feature is the capability to make public or private groups. Groups enable users with the same interests to connect and share content in a more organized setting. Users can join existing groups or make their own based on their interests.
- MeWe also provides a chat feature for person-to-person conversations or group chats. Whether you want to chat with friends or collaborate with colleagues, this feature makes communication flawless.
Conclusion
Registering on MeWe is a very simple process! Users can customize their profiles and the app puts user privacy first. By following these simple steps, you can enjoy using MeWe to the fullest. You’ll meet people who like the same things as you and use a social media site that cares about keeping your information private and giving you control over it.
FAQs
Are there any Joining Fees to be a Part of MeWe?
No, it does not cost anything to use MeWe. You can Join MeWe without giving any fees.
What Information is Required to Join MeWe?
You have to enter very little information when setting up your MeWe account. You have to fill in your first and last name, appropriate email address, and confirm that your age is 16 years. Other than that, sharing any information is your choice and it is optional.
Can I Delete My Account If I Don’t Want to Use MeWe?
Yes! You can easily delete your account! Just tap on your avatar located on the top right side of the page and from the drop down menu click on “Settings.” In settings, under the “My Account” section you will find an option of “Delete My Account”, simply click on it and your account will be deleted.
Read More:
What Is Tether (USDT)? Everything You Need To Know
Tether (USDT) is also known as a “Stablecoin.” It is a cryptocurrency created to provide a stable price point every time. The USDT cryptocurrency was developed by Tether Limited to work as the Internet’s Digital Dollar, with each token valued at USD 1.00 and backed by USD 1.00 in physical reserves.
Numerous blockchain users use it daily to trade, hedge, and transact on different blockchain networks and it doesn’t require a trusted third-party mediator.
In this article, we will learn what is tether USDT?, how it works, and how to use Tether.

What Is Tether (USDT)?
What Is Tether (USDT)?
Tether (USDT) is a stablecoin, it is a type of cryptocurrency that purposefully operates to maintain its valuation stable via market mechanisms. Investors use this to hedge against the indelible volatility of their cryptocurrency investments while still maintaining value in the crypto market, ready to be used easily.
Tether is a fiat-verificatory stablecoin, it is a type of stablecoin that is supported by a fiat currency like USD, CAD, AUD, or even Yen (JPY). Tether was developed to remove the gap between fiat currencies and blockchain assets while providing transparency, stability, and reduced fees for USDT users.
How does Tether (USDT) work?
Each Tether (USDT) issued is supported by one US dollar value of assets. In the beginning, all Tether was issued on the Bitcoin blockchain through the Omni Layer protocol, but currently, it can be issued on any chain that Tether accepts.
Once a tether (a single one of USDT) has been issued, users can use it like any other cryptocurrency token on the chain that it has been allocated. Currently, Tether supports Bitcoin, Ethereum, EOS, Tron, Algorand, and OMG Network Blockchains.
Tether makes use of Proof Of Reserves, which signifies that at any moment their reserves will be equal to or higher than the number of Tether in circulation. Users can verify this on their website.
What Is Special About Tether (USDT)?
Tether (USDT) has been widely accepted and used for years and keeps lawfulness, though often called into question, that few other projects can match. Many vendors and protocols in the blockchain ecosystem use it as a payment option and mode of exchange. Because of Tether’s notable reserves, it doesn’t face any market risks like Black Swan events.
USDT also has the same grandeur as other cryptocurrency tokens on the network, peer-to-peer trading, and PoW or PoS security, this makes it a preferred hedge for traders and users alike.

How To Use Tether (USDT)
How To Use Tether (USDT)
Tether is a stablecoin that can be bought from many popular exchanges. Tether (USDT) can be exchanged for various goods at various vendors or used to exchange for a different currency. Some users will obtain USDT to lend, purchase NFTs, and take part in ICOs. Tether is very versatile and it can be used from anywhere a user wants to transfer or transact value.
How Many Tether (USDT) Coins Are in Circulation?
Tether (USDT) has a circulating supply of 40,805,169,352* USDT tokens. This supply may grow or reduce following the demand and current market liquidity.
Users can purchase USDT tokens on the secondary market or exchanges.
USDT does not accept staking or yield farming for USDT. It should be purchased or issued.
What Gives Tether (USDT) Value?
The purpose of USDT is to offer liquidity and protection against market swings, as its value remains fixed, in concept. The value of Tether (USDT) depends on Tether’s reserves. As long as Tether is backed 1:1 Tether will be valued at 1 US Dollar.
Conclusion
Tether is one of the most famous stablecoins on the market and offers liquidity for transactions worth millions of dollars in value every day. Despite controversies, Tether is a safe choice for users in a volatile market. Millions of people use it for decentralized finance across regions, countries, and continents.
Read More:
USDT vs USDC: What is the difference between these most popular cryptocurrencies in 2024?
Upcoming Notcoin Airdrop: Everything You Need To Know
Why Pepe Coin is Gaining Popularity on MEXC
How to Buy Bitcoin on eToro App: A Comprehensive Guide in 2024
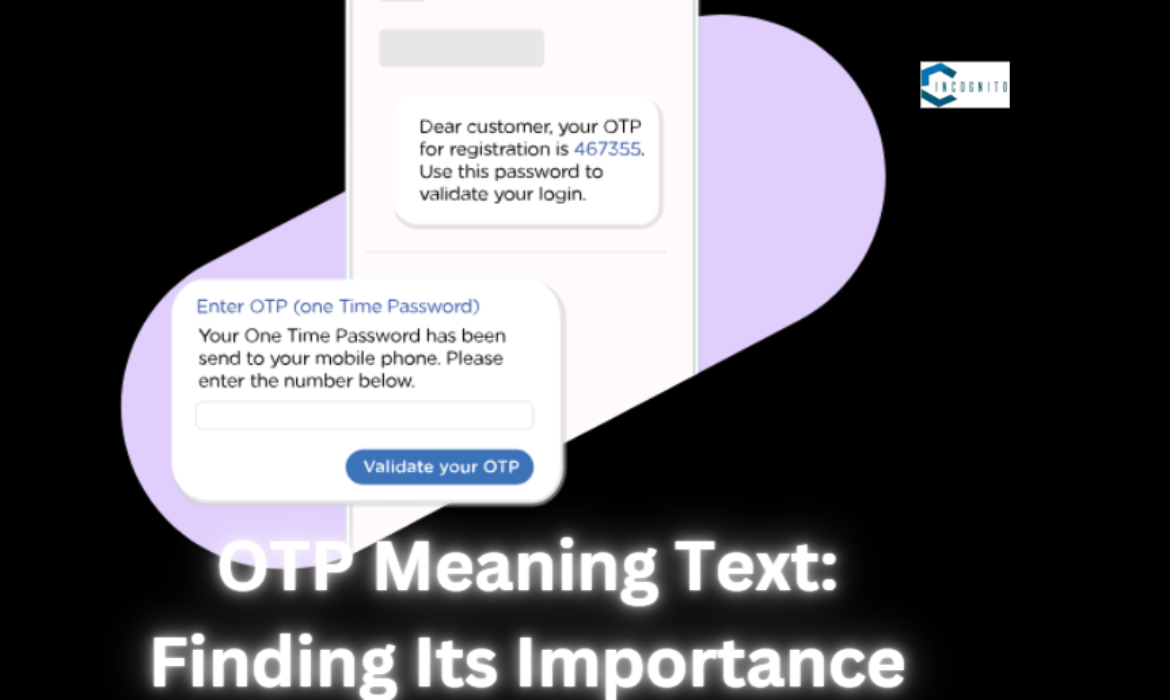
OTP Meaning Text: Finding Its Importance
In the era of digital communication, OTP is widely used, you might be thinking, what does it mean?
OTP is the most regularly and commonly used slang on social media platforms. This abbreviation is used by anyone from young to old people who acknowledge its meaning. The meaning of OTP changes according to the context in which it is being conveyed.
In this article, you’ll understand OPT Text Meaning and its various applications where you can use it and what it means in advanced communication and technology.

What Is Meaning of OTP in Messaging (Social Media)
What Is Meaning of OTP in Messaging (Social Media)
There are various meanings of OTP. However, when we talk about OTP meaning for social media, there is one main meaning. So, let’s talk about what OTP stands for in this scenario.
OTP means “One True Pairing” This term is used on social media to indicate two people who are believed to be best for each other. Fans who love these pairing often show their excitement through pictures, videos, and other forms of media. OTPs can be any pair like romantic couples or best friends who make a great team.
No matter how it looks, an OTP is a special connection that fans feel attached to. It’s not just about admiring two characters; it’s about discovering special things in their chemistry that resonate with us. Whether it’s a perfect relationship, a friendship, an OTP can inspire and bring happiness to fans.
There’s no restriction to the creativity we can use to show our support when it comes to showing our OTPs. We can make fan art, write stories, or even roleplay as our favorite pairs. We can also make use of social media to drive support for our OTPs and share why we love them.
Alternative OTP Meanings
One Time Password
OTP means One-Time Password, a special randomly generated code that is used to confirm a user’s identity or a transaction. It is generally used as an additional layer of security for online accounts and monetary transactions.
On the Phone
OTP also stands for “on the phone,” which signifies right now using the phone. For instance, you can say, “I didn’t catch what you said. I was OTP.”
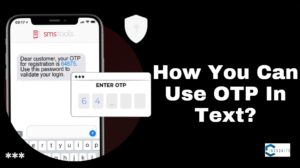
How You Can Use OTP In Text?
How You Can Use OTP In Text?
Convey Your New Found Affection For Someone
OTP, or one true pairing is a term used in fan-created content, media, and social networking to explain a relationship between two characters, usually romantic, that a person believes is best or ideal. It is a method for people to convey their feelings for a specific pairing and to show their support for it.
For Example:
Person 1: “I can’t stop thinking about my OTP from that new show!”
Person 2: “Oh yeah? Which characters are your OTP?”
Convey the feeling of Seeing Your Ideal Couple Together
You can use it to talk about a couple in a movie, book, or real-life relationship. OTP has become the best way for fans who love a particular couple to communicate with each other.
In these types of conversations, OTP is used to define the relationship between two people, whether it is friendly or romantic. It is used to convey appreciation for a couple or hopes for a specific relationship to become a reality.
You can use the OTP to express a rigid opinion on a specific relationship or to express excitement over a particular pairing. It can also be used for expressing solidarity with other fans who want a particular couple to succeed.
For example:
Person 1: “Did you see the new episode? My OTP had a big moment!”
Person 2: “Yes! It was exciting to see them finally confess their feelings!”
Conclusion
OTP is a term that has become very famous on social media, and it’s the best way for people to convey their feelings for the pairing they admire. OTP is a way of expressing appreciation and a lasting reminder that sometimes two people can be ideal for each other.
Read More:
Upcoming Notcoin Airdrop: Everything You Need To Know
Notcoin was launched in January 2024, It is a play-to-earn game on Telegram that enables users to gain rewards in the form of a Notcoin token (NOT) by clicking on the coin icon. NOT is established on the Open Network blockchain (called “TON blockchain”) and is guided by Sasha Plotvinov, the founder of Open Builders, who supervises the development team.
Notcoin Airdrop is made by StarkWare that focuses on enhancing Ethereum’s scalability and efficiency by using zk-rollups, a technology allowing quicker and more economical transactions.

What is Notcoin?
What is Notcoin?
Notcoin is a famous Telegram-based game that includes the “tap-to-earn” mining process. Users can sign up and tap on a gold coin image to obtain in-game rewards.
By finishing quests and tasks, users could unlock extra boosts and prizes. The game obtained massive popularity very quickly, driving numerous players who later got an airdrop of the Notcoin token.
However, as all the coins are now in distribution, the play-to-earn (P2E) game has finished. Notcoin has now set foot into a new phase, progressing to an “explore-to-earn” model, providing users new opportunities to connect with the game and earn rewards via exploration.
Mechanism of the Upcoming Notcoin Airdrop
The Notcoin Airdrop mechanism is centered on a clicker game on Telegram, where users can earn Notcoin tokens via different activities. The much-awaited second airdrop is ready to launch soon on The Open Network (TON). Notcoin recently posted on X (Twitter) that they will carry out a notable airdrop valued at $7 million, with the following information:
- $5 million will be distributed to those who stake and hold levels.
- $2 million will be allocated to users taking part in events over the next three months.
- Moreover, Platinum users will get an average bonus of up to $250.
This airdrop is part of Notcoin’s special influence-based distribution model that will allow users to earn extra rewards by making value for the community. With amazing opportunities and attractive rewards, this event is going to engage a wide range of users and promote active participation.
Tips To Increase Your Profit from this Airdrop
To increase your Notcoin income, follow these tips:
- Use Daily Free Boosts: Grab these free rewards as they fuel your progress towards Silver Tier and unlock the Auto Tap Bot.
- Complete Missions: In the “Earn” tab, users can discover different missions classified as Participate, Special, and Web3 World. Users will the Notcoin as a reward for completing these missions.
- Invite Friends: Invite your friends to join benefits them and also earns you a Notcoin based on how active they are. Premium Users of Telegram get the highest rewards, but even free users can help you collect Notcoin.
- Check For Rewards Regularly: Don’t forget to check the app at least every 12 hours to collect the Notcoin that your Auto Tap Bot has gathered.
- Consistency: Sometimes you can take a break, but don’t be inactive for more than one month. Notcoin has introduced a policy to remove mined coins from inactive accounts before the token launch.

Steps to Secure Your Tokens
Steps to Secure Your Tokens
- Activate Two-Factor Authentication (2FA): Make use of 2FA on all accounts linked to your crypto activities, including your wallet and email.
- Use Effective Passwords: Make unique and difficult passwords for your accounts. Don’t reuse passwords on multiple platforms.
- Backup: Don’t forget to back up your wallet’s recovery phrase on a regular basis and store it in different safe locations.
- Keep Your Software Updated: Make sure your wallet and any related software are always updated to the newest versions to stay safe from vulnerabilities.
Additional Security Measures
Cold Storage: If you are looking for long-term storage, it will be much better if you transfer your tokens to a cold wallet, which is not connected to the internet.
Multi-Signature Wallets: Make use of wallets that require multiple signatures for transactions, adding a layer of protection.
Monitor Transaction: Monitor your wallet for any unauthenticated transactions and take action without making a delay if you observe anything suspicious.
Conclusion
Notcoin, a famous Telegram game, allows users to earn tokens through activities like tapping coins. After its success, it’s moving to an “explore-to-earn” model. A $7 million airdrop on the TON blockchain is upcoming, rewarding those who stake and hold levels, event participants, and Platinum users. Security tips include 2FA and wallet backups.
Read More:
Everything To Know Understand About Clipwise AI
In this modern world, video content is just as significant as blogs or articles. But, making those attractive videos can be difficult and time-consuming. Clipwise AI fills that role! It makes the process of creating videos very easy and simple, allowing you to turn your blog posts, articles, and web pages into attractive videos automatically. In this article we will talk about its features, pricing, and best alternatives.

What is Clipwise AI?
What is Clipwise AI?
Clipwise is an AI-powered platform to help companies and agencies design attractive info videos and sales videos by converting text-based content like blogs, articles, or any URL into a video script, storyboard, and animated video.
By using the advanced and modern technologies, it simplifies the process of video creation, saving time and resources while increasing user engagement.
Features of Clipwise AI
Clipwise AI provides a collection of powerful features to optimize the process of video creation and increase engagement:
AI Viral Script Writer
This feature eases the process of making engaging scripts for your short videos. You just need to define the theme and message you want to convey. By automating the process it saves time and ensures that your content is ready to speak with viewers.
Various Visual Themes
Clipwise AI has a large collection of visual themes, covering virtual reality designs to science fiction. The variety of designs allows users to experiment with various styles to create videos that are ideal for different audiences.
Voice Over Like Human
This feature is made to sound like a human, with the capability to adjust its tone from strong to pleasant and everything in the middle. It doesn’t matter which type of video you want to make, whether it is informative lessons or entertaining storytelling content, its voice-over feature gives a professional touch to your videos.
Mood Based Overlays
To further strengthen the storytelling perspective of your videos. Clipwise AI provides mood-based overlays produced by AI. These overlays are created to enhance the theme and mood of your video by adding visual interest and keenness to your content.

How to use Clipwise AI?
How To Use Clipwise AI?
Step 1: Create your account on clipwise.ai.
Step 2: To start the process, enter your text or the URL.
Step 3: It will process all of your information and create the video that you want.
Step 4: Now, the video will be generated.
Alternatives of Clipwise AI
- Pictory
- AVCLabs
- Kaiber
- Magic hour
- Lumiere AI
- Lalamu studio
- Genmo AI
- D-ID
Pricing
Starter Plan: It is free of cost for all the new users. Users will get 2 videos with watermarks, 3 visual themes, 2 voiceover choices, 3 background music tracks, 1 caption, and 1 overlay animation.
Viral toolkit: It comes with a price of $29, and users can get 20 video credits. Each credit will allow users to create one HD, watermark-free video. By buying this package you will get all the premium features such as a collection of visual themes, professional voice overs, and attractive overlays.

Limitation of Clipwise AI
Limitation of Clipwise AI
- Even though AI technology is very advanced, the quality of scripts, voiceovers, and animation may differ, giving rise to instability or occasional errors in the final result.
- There is a limited level of customization as compared to more advanced editing software.
- Some users may find it unnatural because of the predefined templates and visual themes available. It limits their skills to make unique and customized video content.
- Even though it has a user-friendly interface, learning all the features and functionalities of Clipwise AI may need time and effort.
- While Clipwise AI provides different pricing plans, the ongoing subscription costs may add up over time. The users who don’t use the platform regularly or those on tight budgets may not find it useful.
Conclusion
Clipwise AI is a useful platform for creating YouTube adverts, sales videos, reels, and short video clips. By making use of Clipwise’s AI-driven script writing, visual themes, human-like voiceover, and mood-based overlays features users can create professional videos with ease. However, it is essential to understand possible drawbacks, like variability in quality, limited customization options, and subscription costs.
Read More: